By Pavel Polityuk
KIEV (Reuters) – Hackers from Russia are infecting Ukrainian companies with malware to create so-called ‘back doors’ for a large coordinated attack, Ukraine’s cyber police chief told Reuters on Tuesday, almost a year after a strike on Ukraine spread around the world.
Affected companies range across various industries, such as banks or energy infrastructure. The pattern of the malware being rolled out suggests the people behind it want to activate it on a particular day, Serhiy Demedyuk said.
Demedyuk said his staff were cooperating with foreign agencies to track the hackers, without naming the agencies.
Police had identified viruses designed to hit Ukraine since the start of the year, including phishing emails sent from legitimate domains of state institutions whose systems were hacked, or a fake webpage mimicking that of a real state body.
They had intercepted hackers sending malware from different sources and broken into various components so as to remain undetected by antivirus software until activated as a single unit, Demedyuk said.
“Analysis of the malicious software that has already been identified and the targeting of attacks on Ukraine suggest that this is all being done for a specific day,” he said.
Relations between Ukraine and Russia plunged following Russia’s annexation of Crimea in 2014, and Kiev has accused Russia of orchestrating large-scale cyber attacks as part of a “hybrid war” against Ukraine, which Moscow repeatedly denies.
Some attacks coincided with major Ukrainian holidays and Demedyuk said another strike could be launched on Thursday — Constitution Day — or on Independence Day in August.
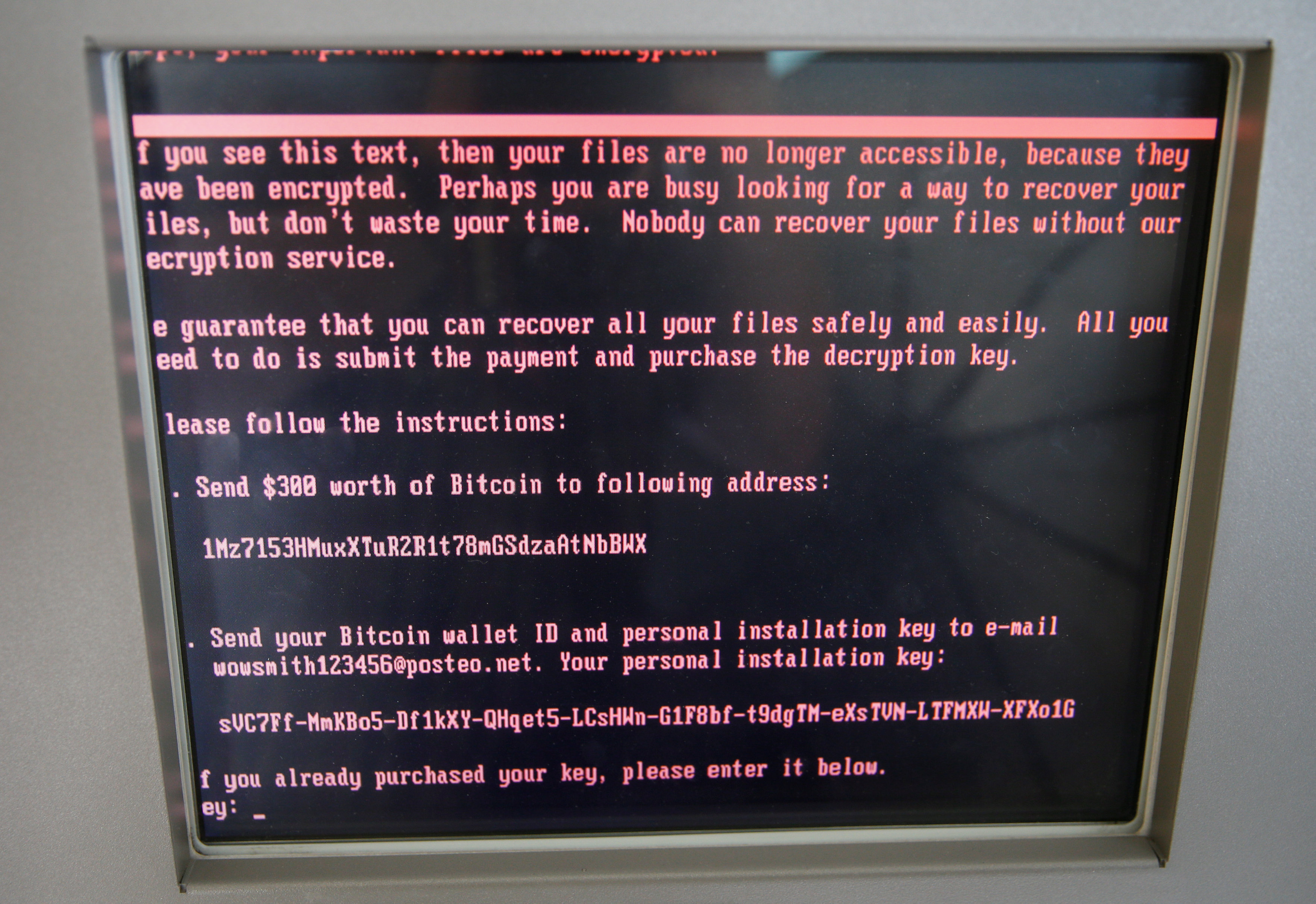
On June 27 last year, the country was hit by a massive strike known as “NotPetya”, which knocked out Ukrainian IT systems before spreading around the world. The United States and Britain joined Ukraine in blaming Russia for the attack.
Demedyuk said the scale of the latest detected preparations was the same as NotPetya.
“This is support on a government level – very expensive and very synchronized. Without the help of government bodies it would not be possible. We’re talking now about the Russian Federation,” he said.
“Everything we’re seeing, everything we’ve intercepted in this period: 99 percent of the traces come from Russia.”
The Kremlin did not immediately respond to a request for comment.
Ukraine is better prepared to withstand such attacks thanks to cooperation with foreign allies since the NotPetya strike, Demedyuk said. Ukraine has received support from the U.S., Britain and NATO among others to beef up its cyber defenses.
But Demedyuk said some Ukrainian companies had not bothered to clean their computers after NotPetya struck, leaving machines still infected by the virus and vulnerable to being used for another attack.
“We are sounding the alarm to remind people – come to your senses, check your equipment,” he said. “It’s better to be on the safe side than clean up a mess like last time.”
He also appealed to global companies who were hit by NotPetya, including U.S. and European firms in Ukraine, to share details of their investigations and steps to localize the hack.
“They have a huge amount of very interesting evidence, which they store themselves. We would like it if they weren’t scared and approached us.”
(Additional reporting by Margarita Popova in Moscow; writing by Matthias Williams; editing by Philippa Fletcher)


