By Jack Stubbs and Pavel Polityuk
MOSCOW/KIEV (Reuters) – A ransomware attack hit computers across the world on Tuesday, taking out servers at Russia’s biggest oil company, disrupting operations at Ukrainian banks, and shutting down computers at multinational shipping and advertising firms.
Cyber security experts said those behind the attack appeared to have exploited the same type of hacking tool used in the WannaCry ransomware attack that infected hundreds of thousands of computers in May before a British researcher created a kill-switch.
“It’s like WannaCry all over again,” said Mikko Hypponen, chief research officer with Helsinki-based cyber security firm F-Secure.
He said he expected the outbreak to spread in the Americas as workers turned on vulnerable machines, allowing the virus to attack. “This could hit the U.S.A. pretty bad,” he said.
The U.S. Department of Homeland Security said it was monitoring reports of cyber attacks around the world and coordinating with other countries.
The first reports of organizations being hit emerged from Russia and Ukraine, but the impact quickly spread westwards to computers in Romania, the Netherlands, Norway, and Britain.
Within hours, the attack had gone global.
Danish shipping giant A.P. Moller-Maersk, which handles one out of seven containers shipped globally, said the attack had caused outages at its computer systems across the world on Tuesday, including at its terminal in Los Angeles.
Pharmaceutical company Merck & Co said its computer network had been affected by the global hack.
A Swiss government agency also reported computer systems were affected in India, though the country’s cyber security agency said it had yet to receive any reports of attacks.
“DON’T WASTE YOUR TIME”
After the Wannacry attack, organizations around the globe were advised to beef up IT security.
“Unfortunately, businesses are still not ready and currently more than 80 companies are affected,” said Nikolay Grebennikov, vice president for R&D at data protection firm Acronis.
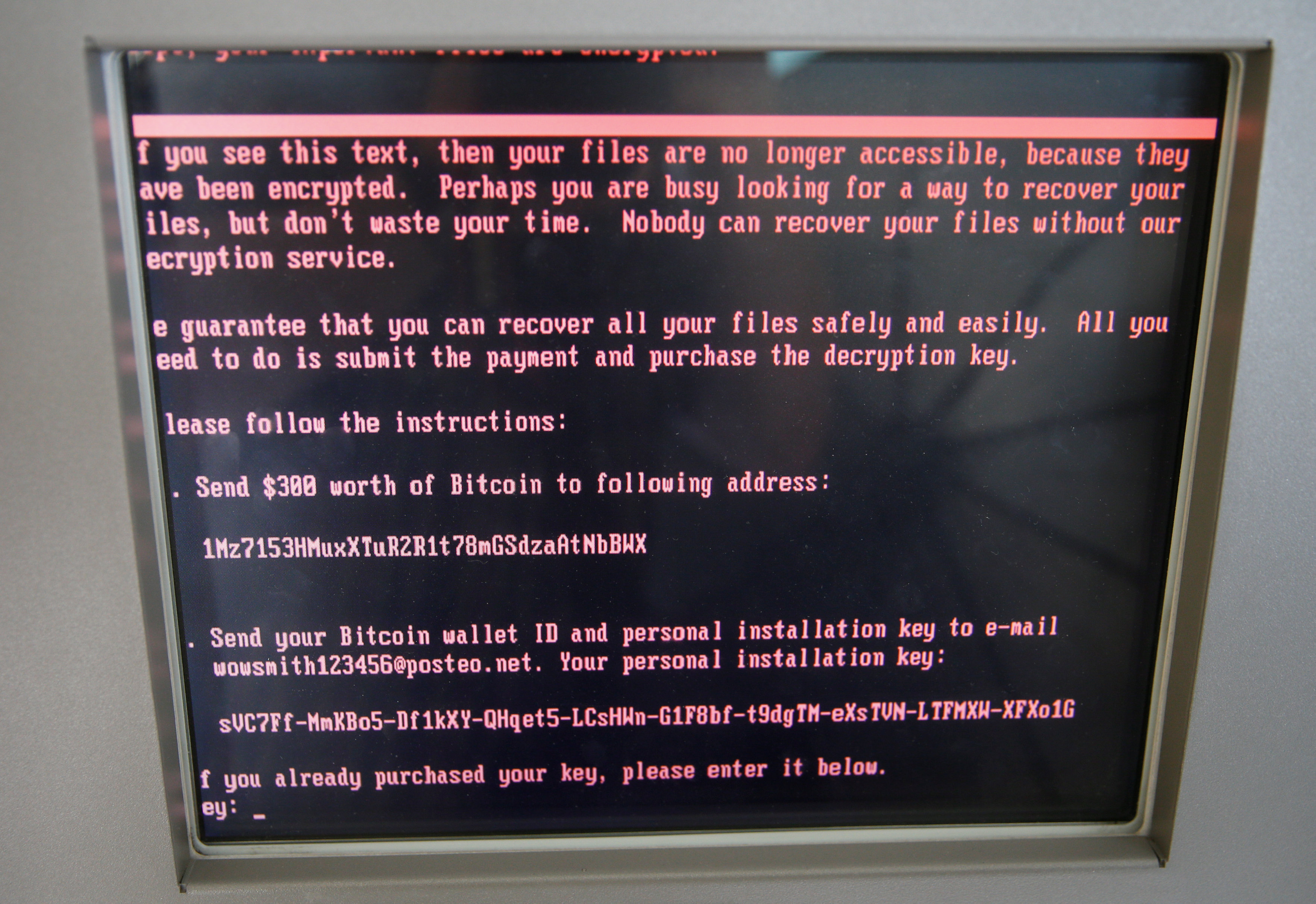
One of the victims of Tuesday’s cyber attack, a Ukrainian media company, said its computers were blocked and it had a demand for $300 worth of the Bitcoin crypto-currency to restore access to its files.
“If you see this text, then your files are no longer accessible, because they have been encrypted. Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service,” the message said, according to a screenshot posted by Ukraine’s Channel 24.
The same message appeared on computers at Maersk offices in Rotterdam and at businesses affected in Norway.
Other companies that said they had been hit by a cyber attack included Russian oil producer Rosneft, French construction materials firm Saint Gobain and the world’s biggest advertising agency, WPP – though it was not clear if their problems were caused by the same virus.
“The building has come to a standstill. It’s fine, we’ve just had to switch everything off,” said one WPP employee who asked not to be named.
WANNACRY AGAIN
Cyber security firms scrambled to understand the scope and impact of the attacks, seeking to confirm suspicions hackers had leveraged the same type of hacking tool exploited by WannaCry, and to identify ways to stop the onslaught.
Experts said the latest ransomware attacks unfolding worldwide, dubbed GoldenEye, were a variant of an existing ransomware family called Petya.
It uses two layers of encryption which have frustrated efforts by researchers to break the code, according to Romanian security firm Bitdefender.
“There is no workaround to help victims retrieve the decryption keys from the computer,” the company said.
Russian security software maker Kaspersky Lab, however, said its preliminary findings suggested the virus was not a variant of Petya but a new ransomware not seen before.
Last’s month’s fast-spreading WannaCry ransomware attack was crippled after a 22-year-old British security researcher Marcus Hutchins created a so-called kill-switch that experts hailed as the decisive step in slowing the attack.
Any organization that heeded strongly worded warnings in recent months from Microsoft Corp to urgently install a security patch and take other steps appeared to be protected against the latest attacks.
Ukraine was particularly badly hit, with Prime Minister Volodymyr Groysman describing the attacks on his country as “unprecedented”.
An advisor to Ukraine’s interior minister said the virus got into computer systems via “phishing” emails written in Russian and Ukrainian designed to lure employees into opening them.
According to the state security agency, the emails contained infected Word documents or PDF files as attachments.
Yevhen Dykhne, director of the Ukrainian capital’s Boryspil Airport, said it had been hit. “In connection with the irregular situation, some flight delays are possible,” Dykhne said in a post on Facebook. A Reuters reporter who visited the airport late on Tuesday said flights were operating as normal.
Ukrainian Deputy Prime Minister Pavlo Rozenko said the government’s computer network had gone down and the central bank said a operation at a number of banks and companies, including the state power distributor, had been disrupted by the attack.
“As a result of these cyber attacks these banks are having difficulties with client services and carrying out banking operations,” the central bank said in a statement.
Russia’s Rosneft, one of the world’s biggest crude producers by volume, said its systems had suffered “serious consequences” from the attack. It said it avoided any impact on oil production by switching to backup systems.
The Russian central bank said there were isolated cases of lenders’ IT systems being infected by the cyber attack. One consumer lender, Home Credit, had to suspend client operations.
(Additional reporting by European bureaux and Jim Finkle in Toronto; writing by Christian Lowe; editing by David Clarke)